
Option A - Databases
Question 1
SLPaper 2A school maintains a database of students’ details and teaching resources on a central server. This data can be accessed by all teachers in the school.
Teachers may need to edit resources when preparing their lessons.
When storing student details, data security is an important consideration.
The school has appointed a database administrator (DBA).
A DBA is required to carry out tasks such as ensuring there is a strategy to recover the database if it becomes corrupted and that the data is shared ethically.
Explain how concurrent use of the school database is possible in this situation.
Describe two ways that data security in the school's database can be maintained.
Describe one strategy that could be used to ensure the data can be recovered if the database becomes corrupted.
Suggest how the privacy of student data can be ensured.
Question 2
SLPaper 2Consider the following example relation. It holds data about a number of teachers and students from different schools who volunteer to support the local community on particular days.
SCHOOL_VOLUNTEERS_TABLE (School_Name, Code, Address, Date, Num_Volunteers)
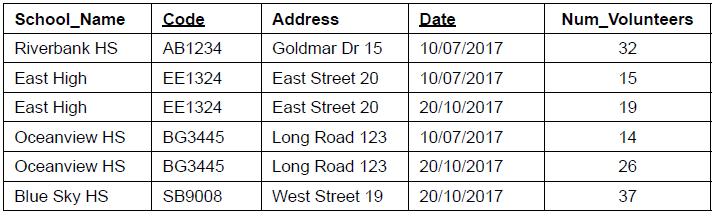
The key attributes are underlined.
State what is meant by redundant data in databases.
Explain one issue that can be caused by redundant data in a database.
Identify three characteristics of the 1st Normal Form (1NF) which are evident in this relation.
Explain why a compound key is used for the SCHOOL_VOLUNTEERS_TABLE relation.
The following shows the normalized SCHOOL_VOLUNTEERS_TABLE relation:
SCHOOLS_TABLE
Code, School_Name, Address
VOLUNTEERS_TABLE
Code, Date, Num_Volunteers
Discuss whether these relations are in third normal form (3NF).
Question 3
SLPaper 2Define the term database management system (DBMS).
Identify three characteristics of logical schema.
Outline the purpose of a data definition language (DDL).
Identify two tasks that a database administrator carries out to ensure the security of the database.
Question 4
SLPaper 2Define the term database transaction.
Explain the importance of durability in a database transaction.
Identify two different types of relationships within databases.
Describe the nature of the data dictionary.
Identify four responsibilities of a database administrator.
Question 5
HLPaper 2A telecommunication company stores a large amount of data in three databases.

The database segmentation is carried out on the CUSTOMERS database.
Data mining is used to extract knowledge hidden in this large amount of data. Before using data mining processes the existing data should be cleaned up.
Customers committing fraud is a risk to the company.
Evaluate the use of an object-oriented database as opposed to a relational database.
Define a spatial database.
State what is meant by database segmentation.
Explain one benefit of database segmentation to the telecommunication company.
Explain how ETL processes could be used in data preparation.
Distinguish between the use of association and sequential patterns as data mining techniques.
Describe how deviation detection could be used to detect fraud at the telecommunications company.
Customers who decide to leave the telecommunication company for a competitor may result in huge losses for the telecommunications company.
Explain with the use of an example, how predictive modelling could be used to optimize information sent to existing customers.
Question 6
SLPaper 2Outline the difference between an information system and a database.
A bank maintains a database that stores details of clients and their accounts.
A client wants to transfer money between two accounts held at the same bank.
Explain how the ACID (Atomicity, Consistency, Isolation, Durability) properties would apply in the context of this database transaction.
A bank holds large volumes of financial and personal information about its clients in its database.
Discuss whether this database should be open to interrogation by the police or the Government.
Question 7
SLPaper 2Armour Hardware Company has the following data about salespersons and the quantities of items sold.
Each salesperson can sell many different products.
SALES_PERSON
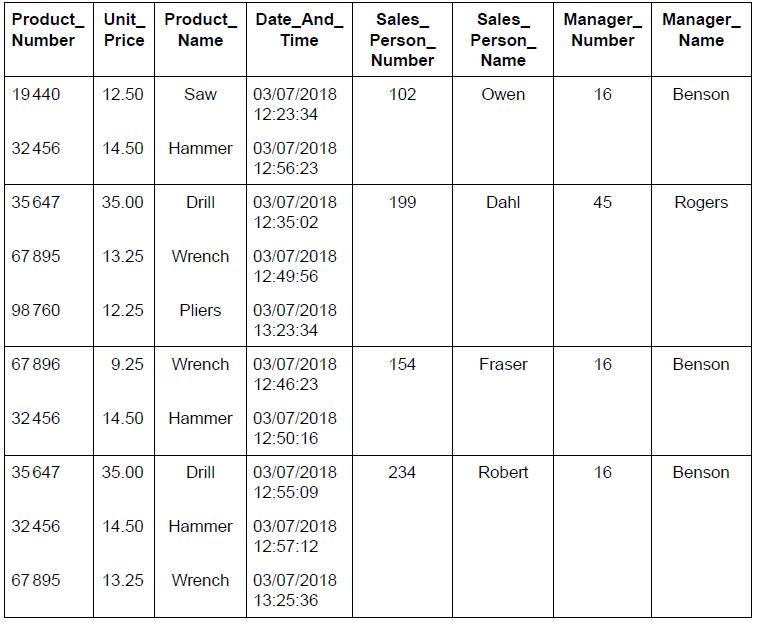
Outline two reasons why databases are normalized.
Outline why the SALES_PERSON table is not in 1st Normal Form (1NF).
Construct the 3rd Normal Form (3NF) of the unnormalized relation shown above.
Outline why it is necessary to ensure that referential integrity is maintained in databases.
Outline why a primary key may consist of more than one attribute.
Question 8
HLPaper 2The collection, storage and sharing of data is becoming increasingly important for organizations who have a choice about which type of database to use to store their data. Two examples of database types are relational and object-oriented.
The 2016 US presidential election was seen to be a victory for data analytics. Companies that specialize in analytics use data warehouses.
Explain two advantages of using a relational database rather than an object-oriented database.
State two characteristics of a data warehouse.
Outline why data needs to be transformed before it can be loaded into the data warehouse.
Outline why opinion poll data and other election data are timestamped when added to the data warehouse.
Outline why analytics companies use link analysis.
Outline why analytics companies use deviation detection.
Once data has been loaded into a data warehouse it can be mined. The use of data analytics is believed to have been important to the outcome of the US election campaign.
Discuss whether the advantages of data mining techniques in this scenario outweigh the disadvantages.
Question 9
HLPaper 2ZCC has a chain of offices that sell different types of paper to customers all over the world. They have data stored in their data warehouses that will help them make important marketing decisions for the future, as they have plans to diversify into other products like gift-wrappers, scribble-pads, stationery, books and calculators.
ZCC is going to use data mining techniques to discover patterns in their data.
The company has customers who have missed the payment deadline for their purchases from ZCC.
Outline why data warehousing is time dependent.
Outline one reason why ZCC uses a data warehouse.
Outline why transformation of the data is necessary prior to it being loaded into the data warehouse.
Compare cluster analysis and classification as techniques for discovering patterns in_ZCC_'s data.
Describe how the process of deviation detection can be applied to identify customers who are likely to miss the payment deadline for their purchases from ZCC.
ZCC is aware that other data mining and detection techniques will allow more informed marketing decisions to be made.
Explain how database segmentation and link analysis can be used by ZCC to improve their marketing strategies.
Question 10
SLPaper 2One-to-7 is an international organization that works with teachers and other educators. One department within this organization provides an online forum for teachers to discuss ideas for lessons and to share resources.
In order to access this forum teachers are required to submit the following information, which will be stored in a table in the database.
Figure 1: Online form to register personal details to the One-to-7 forum

Once the submit button on the online form has been selected, the personal data is input into the database.
Once the teacher is registered they can post comments on the forum.
The One-to-7 database in managed by the database administrator (DBA).
Identify one reason why the teacher’s name has been split into two fields.
Outline one reason why there may be concerns about the amount of personal information that is requested.
Outline why the transaction needs to be atomic in the context of this scenario.
Explain how transactions are managed to ensure isolation when registered teachers add comments to a discussion thread on the forum.
Identify two tasks that are carried out by the database administrator (DBA).
The DBA is considering using the email address as the primary key, but is concerned that many of the 250 000 educators who are registering for this online forum may have more than one email address. Users may create duplicate accounts, deliberately or accidently, by using different email addresses as usernames.
Explain the factors that would need to be considered in using a composite primary key instead of only using the email address.
