
Option C - Web science
Question 1
HLPaper 2Many city authorities have realised the opportunities that social media and collective intelligence can provide.
Narayan City is considering using data gathered from citizens using traffic apps on their GPS-enabled mobile devices to help plan future changes to the layout of the road network in and around the city.
Outline one advantage for Narayan City of using collective intelligence to solve complex problems such as changing the layout of roads.
Many social networking sites allow users to classify their posts and responses, for example by adding one or more “hashtags”.
To what extent does the increasing number of social networking sites and the creation of folksonomies contribute to web users modifying their online behaviour?
Question 2
SLPaper 2The internet and World Wide Web are often considered to be the same, or the terms are used in the wrong context.
Many organizations produce computer-based solutions that implement open standards.
A search engine is software that allows a user to search for information. The most commonly used search algorithms are the PageRank and HITS algorithms.
Distinguish between the internet and the World Wide Web.
Outline two advantages of using open standards.
Outline why a search engine using the HITS algorithm might produce different page ranking from one using the PageRank algorithm.
Web crawlers browse the World Wide Web.
Explain how data stored in a meta-tag is used by a web crawler.
Question 3
SLPaper 2Pugh University has a website that allows computer science students to enter their name and customize the web pages.
Consider the section of HTML and CSS code shown below.
File name: index.html
<!DOCTYPE html>
<html>
<body>
<script>
function setVar(){
var subject=document.getElementById('kippers').value;
document.getElementById('subj').innerHTML = subject;
}
</script>
<h2>My First Page</h2>
<p>Welcome to the <span id='subj'></span> Faculty</p>
<input type='text' id='kippers'/>
<button onclick='setVar();'/>clickme</button>
</body>
</html>
When a student enrolls, they must enter their name on a web page. Before being added to the database, the system should check that the name typed is not blank and that it has not already been added to the database.
Consider the following URL:
The common gateway interface (CGI) offers a standard protocol for web servers.
State the output of the index.htmlfile in the web browser.
Describe the processing that takes place when the user inputs “Pugh” into the text box and then uses the clickmebutton.
Explain why these two validation checks occur on different computer systems.
Explain how website certificates are used to authenticate a user’s browser through secure protocol communications like HTTPS.
Describe the working of the common gateway interface (CGI).
Pugh University uses cloud computing services, such as Google Docs or Office 365.
Describe how cloud computing is different to a client–server architecture.
Question 4
SLPaper 2BesTea is a company that sells tea and tea-related accessories online. Users browsing the website encounter the following URL:
https://www.BesTea.com/customer/pages/delivery
A person enters the URL for BesTea into their browser.
The logos of the credit and debit cards accepted by BesTea are displayed as images in the footer of all of its web pages.
The BesTea website includes a shopping basket facility that enables users to make purchases.
The following fragment of PHP code is present in the script that allows users to place a completed order:
query ('SELECT \* FROM users\_db WHERE id = ' .$\_SESSION\['sessionUserID'\]); $userRecord = $query -> fetch\_record(); … \>Describe how this URL provides security in communication over the Internet.
Identify the steps that the Domain Name System (DNS) server will take in order to locate the correct IP address for this request from the browser.
Outline how the footer of a web page can be made identical across all pages of a website.
Suggest the function of this fragment of code.
Users may perform several actions on their shopping baskets. These actions require interaction with a central database of products. Each record in this database includes the identifier, the name and the price of one of these products.
Consider the following fragment of code:
<
$basket = new Basket
…
If \_REQUEST\['action'\] == 'removeBasketItem' && !empty(_REQUEST['id']){
remove(_REQUEST['id']);
header('view_basket.php');
}
>
From the code, identify the information that the user has provided.
Question 5
SLPaper 2Open source code is made available by a community of developers and is frequently updated. The code can be downloaded for free, but users must register with the website and have their access authenticated.
Authentication is based on signing in to an established third-party company, for example a user’s existing email or a social network account. The third-party company then verifies the user, granting them access to the open source code website.
The URL of this website is www.OpenSourceDev.org. Any new pieces of code that the developers make available become new resources on the website. A script generates weekly automatic notifications of new code available on the site, and sends this notification to users as an email.
Evaluate the use of server-side scripting to provide the mechanism for registration.
Explain how the user’s privacy can be maintained whilst using this method of authentication.
Outline, with an example, how the URL for these new pieces of code will be generated.
Outline the steps that the script could perform for sending out these notifications.
A fragment of a script and a web form are provided below.
In the script some functions are not implemented, and only their specification is provided.
Describe the processing that occurs when the form is filled with the URL https://www.the2nd.org/bin.php?id=70 that the server discovers is associated with the IP address 172.16.254.1.
Question 6
HLPaper 2With reference to the bowtie model of the web, consider the following graph. It represents a snapshot of popular sites about a specific topic.

After two months, the graph has evolved into the one shown below.
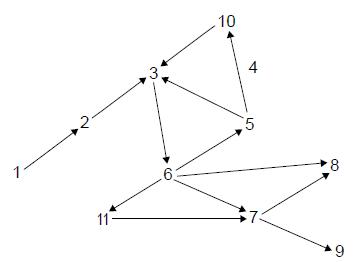
We can interpret the graph as follows:
Each node represents a document and each outgoing arrow represents a hyperlink in the document.
Identify the nodes in the strongly connected core.
Identify the set of OUT nodes.
Outline why the edge between node 2 and node 1 is a tendril.
Identify two reasons why an edge may disappear in the new graph, for example the edge between node 5 and node 4.
State how many hyperlinks are in the document corresponding to node 6.
Power laws are often used to model phenomena occurring in very large networks and predict their evolution. Power laws may be suitably applied in different cases, in the context of the World Wide Web.
With reference to the relation between the number of documents in the web and the number of hyperlinks in each of them, suggest how power laws may help to explain the shape of the World Wide Web.
Question 7
SLPaper 2A web application (app) runs on mobile devices such as smartphones and tablets. It allows users to locate their position in real time on a map, as they walk around a city, as well as the surrounding attractions. The app uses icons to represent tourist attractions such as art galleries and museums. When the user clicks on the icon, further details are shown, such as opening times. The app includes some use of client-side scripting.
Many art galleries have websites that can be found by search engines. White hat techniques and practices allow website developers to optimize the search process. It is good practice to maintain the source code of websites up-to-date with actual information.
Outline the functioning of this app. Include specific references to the technology and software involved.
With reference to the use on mobile devices, outline a feature of this application that may rely on client-side scripting.
State two metrics used by search engines.
Explain why maintaining a clean HTML source code of a website by removing old information optimizes the search process.
The evolution of the web, architectures, protocols and their uses has led to increasingly sophisticated services that run on peer-2-peer (P2P) architectures.
Explain how a P2P network can provide more reliability than a client-server model.
Question 8
HLPaper 2An international organization, OBI, has three offices in Europe, see Figure 7.
Figure 7: The location of OBI’s offices in Europe

[Source: adapted (recoloured, cropped and annotated) Europe Map by Erin Dill 0, www.freevector.com.
Under copyright and CC 4.0 licence (https://creativecommons.org/licenses/by-sa/4.0/)\]
Office A and Office B report to Office C, the head office.
Office A and Office B collaborate on many projects. Office C is not involved in the collaboration between Office A and Office B.
OBI has projects that involve large numbers of contributors from all over the world. These projects are managed by OBI staff in Office A.
The contributors often include non-text based information.
Draw a directed graph based on the scenario.
Describe the role of graph theory in determining the connectivity of the World Wide Web.
Outline two issues that may arise from using a non-text based search.
OBI has decided to gather information for one project by utilizing collective intelligence.
Evaluate this decision.
Question 9
HLPaper 2Smart technologies can be used to illuminate the night. Street light intensity and coverage can both be controlled, depending on physical parameters, such as the time of the day, or weather conditions.
The amount of pedestrians in the street or their activities could be further parameters used by algorithms for these type of applications.
Discuss the technologies that ambient intelligence uses in this specific scenario.
With a focus on privacy, discuss how traffic data from WiFi communication through smartphones can be used in this scenario.
Question 10
HLPaper 2Southend Council in England is considering whether to use Pepper, a humanoid robot, to assist some elderly residents that live in care homes. These elderly residents suffer from memory loss and would rely on Pepper to direct them them to and from the local shops. Pepper uses ambient intelligence and is connected to the Internet of Things (IoT).
Explain why Southend Council may have concerns about introducing Pepper for this purpose.
